Introduction
In the digital age, where connectivity reigns supreme, understanding the diverse landscape of computer networks is not just beneficial but essential. These networks are the digital threads that keep us connected, serving as the backbone of our modern society and transforming the way we live, work, and play.
In this blog post, we won’t just gain knowledge; we’ll also unlock the true power of computer networks and explore the seven key variations. Whether you’re a technology enthusiast, an aspiring IT professional, or simply someone who has recently embarked on exploring the magic of the internet, this exploration promises to shed light on the different types of computer networks that power our digital world from dawn to dusk.
So, get ready to dive deep into the intricacies of these networks and uncover how they function.
Table of Contents
What is computer network?
Define Computer Network:

A computer network is a system of interconnected computers, devices, and nodes that are linked together to share resources and information. It allows for the efficient exchange of data, communication, and collaboration among users and systems, whether they are in the same location or separated by vast distances.
Concept of Computer Network:
Connecting computers and devices is at the core of what a computer network does. It involves establishing a communication channel between these entities, which can be achieved through physical cables or wireless technology.
This connectivity, which in turn facilitates the exchange of data and communication, and overall allowing us to send emails, browse websites, share files, and even connect with people worldwide through video calls etc.
Significance of Computer Networks:
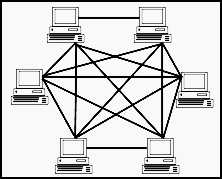
The significance of computer networks in our digital world cannot be overstated. They form the foundation of modern communication, connecting individuals, businesses, and institutions globally.
These networks enable the smooth functioning of the internet, e-commerce, social media, and much more. They enhance productivity by facilitating remote work and collaboration, while also driving innovation in fields like healthcare, education, and entertainment.
In essence, computer networks are the invisible force that powers our interconnected, information-driven society.
Advantages and Disadvantages of Computer Networks
| Advantages | Disadvantages |
| Resource Sharing. In computer networks, resource sharing allows multiple users to access shared resources such as printers and files. This promotes efficiency, reduces redundancy, and facilitates seamless collaboration by enabling users to access and utilize these resources from various locations within the network. | Security Concerns Computer networks are vulnerable to cyber threats as they provide potential entry points for malicious actors to infiltrate and compromise sensitive data or disrupt operations, making network security and vigilance paramount in safeguarding against a wide range of cyber attacks. |
| Improved Communication Computer networks enhance communication by facilitating seamless data exchange and collaboration among networked systems, promoting efficient and real-time information sharing across diverse locations and devices. | Maintenance Costs. Network maintenance can be costly, given the expenses associated with ensuring the network’s optimal performance, regular updates, security measures, and the need for skilled IT professionals to manage and troubleshoot any issues that may arise. |
| Centralized Data Management Computer network helps in centralizing data storage and management. | Scalability Challenges. Expanding networks can be complex and require careful planning. |
Components of a Computer Network
1. Devices that consist of Computer network:
Computers, mobiles, and other consumer devices:

- Individual computers, like laptops and desktops, play a crucial role in a network as they are the devices we use to access and interact with information and resources on the network.
- For example, when you browse the internet on your laptop or send emails from your smartphone, you’re using these devices to connect to the network and retrieve or send data.
Servers:
- Servers are like the powerhouse of a network. They store and manage important data and resources that other devices in the network need.
- For instance, when you access a website, you’re actually connecting to a server that stores the webpages and delivers them to your computer. Servers ensure that information is organized and accessible to everyone on the network.
Networking Hardware:
- Networking hardware includes devices like routers, switches, gateways, and cables.
Routers:
Devices that direct data traffic within a network, ensuring it reaches the correct destination.
This router directs data traffic within a home or office network, ensuring devices like laptops, smartphones, and smart TVs can access the internet and communicate with each other.
Product Example: Linksys AC1750 Dual-Band Wi-Fi Router
Switches:
Devices that connect multiple devices within a network, facilitating seamless communication between them.
A switch like this connects multiple devices, such as computers, printers, and IP cameras, in an office network, allowing them to communicate and share resources.
Product Example: Cisco Catalyst 2960 Series Ethernet Switch
Gateways:
Entry points that link local networks to the broader internet, allowing access to online resources.
Gateways like this serve as the entry point between a home network and the internet. They translate data between the local network and the worldwide web, enabling users to access websites, stream content, and more.
Product Example: Netgear Nighthawk AX12 12-Stream Wi-Fi 6 Router
Cables:
Physical connections that transmit data between devices and networking components, forming the network’s infrastructure.
Ethernet cables like CAT6 physically connect devices to a network. They can be used to connect a computer to a router or to link networking components like switches, ensuring data transmission between them.
Product Example: CAT6 Ethernet Cable
General Hosts:
- A general host refers to any device on the network that isn’t a server or specialized networking equipment. These devices, like your laptop, smartphone, or smart TV, are like the network’s “users.”
- They use the network to access data, browse websites, send emails, or perform other tasks. General hosts are the ones benefiting from the resources managed by servers and the connectivity provided by networking hardware.
2. Types of Linking Devices: Wired and Wireless
Wired Linking Devices:
- Wired linking devices use physical cables to connect different things together in a network. It’s a bit like how your headphones connect to your phone with a wire. One example of a wired linking device is an Ethernet cable, which connects your computer to the internet router.
- Another example is a USB cable that links your phone to your computer to transfer photos and videos.
Wireless Linking Devices:
- Wireless linking devices, on the other hand, don’t need any cables. They use invisible signals, like Wi-Fi or Bluetooth, to connect things.
- For instance, Wi-Fi allows your laptop to connect to the internet without plugging in any cables. Bluetooth connects your wireless headphones to your phone so you can listen to music without wires.
So, in a network, you can have things connected with cables (wired) or without cables (wireless), and both types of linking devices help make it all work smoothly.
Communication Protocols and Layers:
A communication protocol is like a set of rules that all devices in a network follow when they’re sharing information. It’s a bit like everyone agreeing on a common language to talk to each other.
Some common communication protocols include:
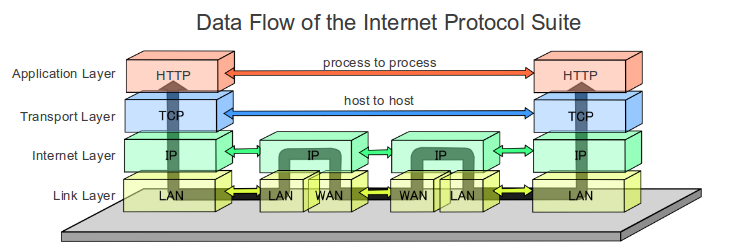
Internet Protocol Suite (TCP/IP): Think of this one as the big boss of protocols. It’s like the master guide that helps devices on the internet understand each other. It’s a bit like a universal translator for the web.
IEEE 802: This one is like a rulebook for wireless communication. It helps devices like laptops, smartphones, and even some smart home gadgets connect to the internet without any wires. It’s a bit like a set of instructions for having a smooth conversation without shouting across the room.
Ethernet: Ethernet is like the foundation of many wired networks. It’s the cable and connection system that helps computers and other devices talk to each other within a local network, like in an office.
Wireless LAN: This is a set of rules for Wi-Fi, which is like the magic that lets your laptop or phone connect to the internet without any cords. It’s a bit like the secret sauce that makes your favorite dish taste amazing.
Cellular Standards: Think of cellular standards as the rulebook for your mobile phone. They’re what allow your phone to connect to the cell towers and make calls or use the internet while you’re on the go.
Computer network consist of different layers as listed below:
Network Access Layer:
- Imagine this layer as the gatekeeper of your network. It helps devices connect to the network and controls how they send and receive data. Think of it like the entrance to a club where you need to show your ID (or in this case, network credentials) to get in.
Internet Layer:
- The internet layer is like the postal service for your data. It decides how data packets should travel across the vast network of networks that make up the internet. It’s a bit like a GPS guiding a package to its destination, making sure it goes to the right place.
Transport Layer:
- This layer is all about ensuring your data arrives intact and in the right order. It’s like a delivery service that takes extra care to make sure nothing gets lost or jumbled during the journey. It also decides how fast or slow data should be sent.
Application Layer:
- Think of the application layer as the software that makes everything happen on your device. It’s like the apps on your phone or computer. This layer deals with things like sending emails, browsing websites, or streaming videos. It uses the lower layers to make sure these applications can communicate over the network smoothly.
Network Defence: Protecting the Digital fort.
Network defense is all about safeguarding your digital world from cyber threats and attacks. It’s like building strong walls, setting up guards, and having a powerful firewall around a medieval castle to protect it from invaders.
In the world of computers and networks, network defense involves using various strategies and tools to secure your data, devices, and the network itself. This includes things like firewalls, antivirus software, intrusion detection systems, and regular software updates.
A firewall, in particular, acts as the first line of defense. It’s like a vigilant sentry at the castle gate, allowing only authorized traffic to enter and blocking malicious or unwanted data, as result creates a barrier protecting your information from falling into the wrong hands.
5. Seven Types of Computer Networks
PAN (Personal Area Network)
- Definition: A PAN, or Personal Area Network, is a small network designed for personal devices like smartphones, laptops, and tablets. It covers a very short range, typically within a few meters.
- Use Cases: PANs are used for connecting devices within a close proximity, such as wirelessly connecting your smartphone to your wireless headphones or syncing your smart watch with your phone.
MAN (Metropolitan Area Network)
- Explanation: A MAN, or Metropolitan Area Network, is a network that covers a larger geographical area than a LAN but smaller than a WAN. It typically spans a city or a large campus.
- Examples: MANs are commonly used by businesses or institutions to connect multiple buildings within a city, facilitating efficient data sharing and communication between them.
WAN (Wide Area Network)
- Description: WANs, or Wide Area Networks, are extensive networks that can cover large geographic areas, even spanning across countries or continents. They connect LANs and MANs over long distances.
- Importance: WANs are crucial in the digital age as they enable global connectivity and underpin the functioning of the internet. They facilitate data transfer, communication, and resource sharing on a global scale.
LAN (Local Area Network)
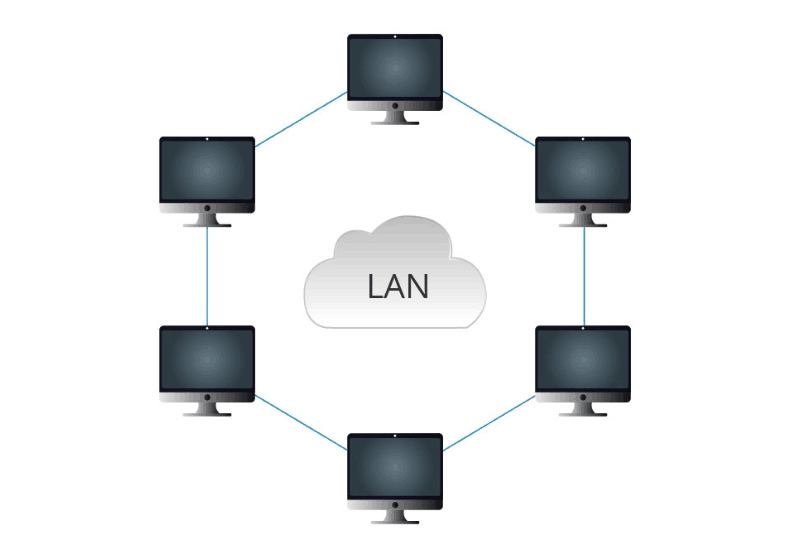
Definition: LANs, or Local Area Networks, are small-scale networks used within a limited physical area, such as a home, office, or campus. They connect devices like computers and printers.
- Common Use: LANs are commonly used in homes and businesses for sharing resources like printers, files, and internet connections. They promote local communication and collaboration.
VPN (Virtual Private Network)

- Description: VPNs, or Virtual Private Networks, provide secure and private connections over a public network, typically the internet. They create encrypted tunnels for data transmission.
- Role in Security: VPNs play a vital role in securing network communications, especially in remote work scenarios. They safeguard sensitive data, maintain privacy, and protect against cyber threats.
- Benefits: Using a VPN offers benefits such as enhanced security, anonymous browsing, and the ability to access geo-restricted content.
Storage Area Network (SAN)
- Function: SANs are specialized networks dedicated to high-speed data storage and retrieval. They are commonly used in enterprise environments to centralize and manage data storage.
Cloud Network
- Concept: Cloud networks refer to networks of servers and data storage systems hosted on the internet (the cloud). These networks provide scalable resources and services on-demand.
- Ubiquity: Cloud networks are prevalent today, enabling businesses and individuals to access a wide range of cloud-based services, including data storage, software applications, and infrastructure, from anywhere with an internet connection.
6. Network Topologies: Shaping the Network Structure
Overview of Network Topologies: Network topologies define the physical or logical layout of a computer network. They determine how devices are connected and how data flows within the network. Just like the blueprint of a house outlines the arrangement of rooms and hallways, network topologies provide the framework for data transmission and communication among devices.
Eight Common Types of Network Topologies:

- Devices are connected in a linear fashion along a single cable (the “bus”).
- Simple and cost-effective but can be prone to data collisions.
- Star Topology:
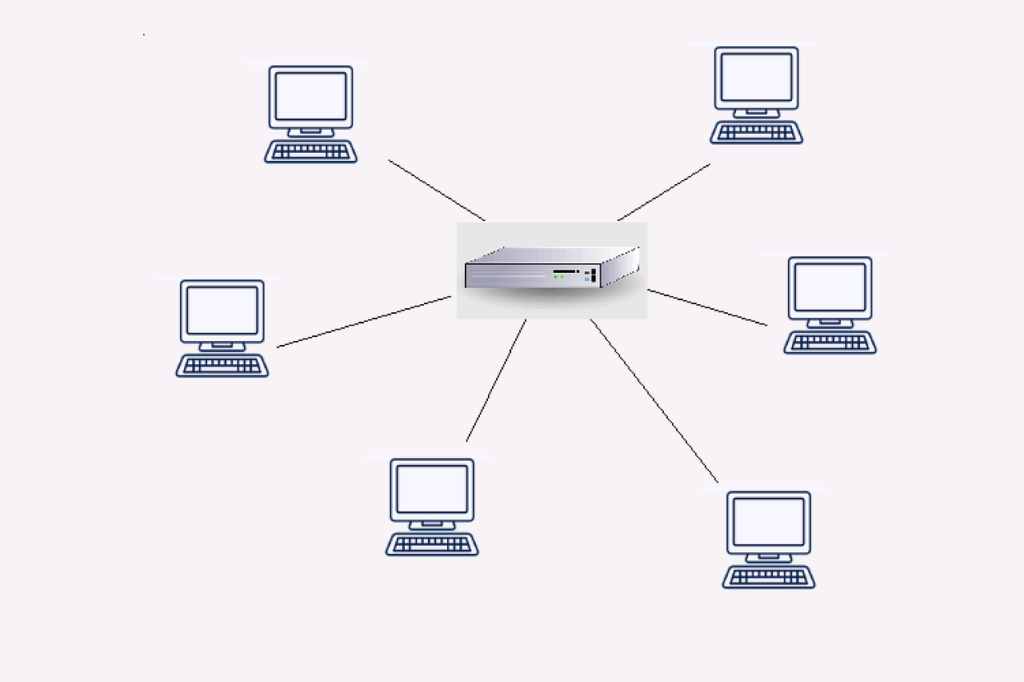
- All devices are connected to a central hub or switch.
- Ensures efficient data flow and easy troubleshooting, but relies heavily on the central hub.
- Ring Topology:
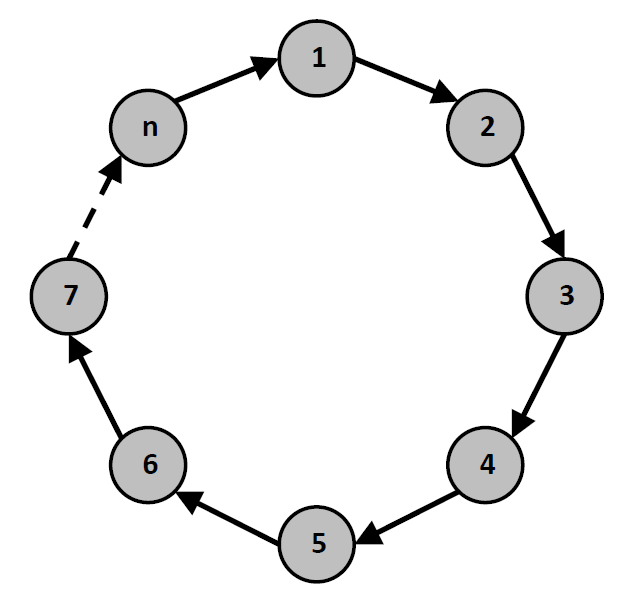
- Devices form a closed loop, with each device connected to exactly two others.
- Offers redundancy and stable data transmission but can be challenging to expand.
- Mesh Topology:
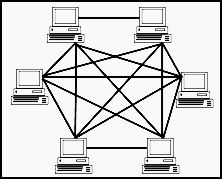
- Every device is connected to every other device in the network.
- Ensures robustness and redundancy but requires a lot of cabling and can be complex to manage.
- Tree Topology:
- A combination of star and bus topologies, where groups of star-configured networks are connected to a linear bus backbone.
- Offers scalability and organization but can be challenging to set up.
- Hybrid Topology:
- Combines two or more different topologies within a single network.
- Offers flexibility and customization but can be complex to design and maintain.
- Point-to-Point Topology:
- Connects two devices directly to each other.
- Commonly used for simple, dedicated connections, such as linking two offices.
- Daisy Chain Topology:
- Devices are connected in a linear manner, similar to a chain.
- Often used in simple setups, but if one device fails, it can disrupt the entire chain.
Each of these network topologies has its advantages and disadvantages, making them suitable for different scenarios and requirements. The choice of topology depends on factors like the network’s size, complexity, scalability needs, and the importance of redundancy and fault tolerance.
7. Network Devices making famous company list
| Network Device | Famous Companies |
| 1. Router | Cisco, Juniper Networks, NETGEAR, TP-Link |
| 2. Switch | Cisco, Juniper Networks, Arista Networks, HPE, Dell EMC |
| 3. Firewall | Palo Alto Networks, Cisco, Fortinet, Check Point |
| 4. Modem | ARRIS, Motorola, Netgear, Linksys |
| 5. Access Point (AP) | Netgear, Ubiquiti, Cisco, Aruba Networks, TP-Link |
| 6. Network Attached Storage (NAS) | Synology, QNAP, Western Digital, Buffalo |
| 7. Load Balancer | F5 Networks, Citrix, Radware, A10 Networks |
8. The Internet and Its Dependence on Networks
The internet, often described as a vast global network of networks, heavily depends on computer networks to function effectively. Think of the internet as a superhighway where data travels between devices and servers. These data packets need well-structured pathways, which are provided by computer networks.
Without networks, the internet would be a chaotic mess, akin to trying to navigate a city without roads or traffic rules.
Networks are the fundamental building blocks of the internet. They ensure data gets from one place to another, connecting users across the globe. This connectivity allows us to access websites, send emails, stream videos, and engage in countless online activities.
Computer networks route data accurately, maintain stability, and provide security, which are critical for the internet’s smooth operation. In essence, without networks, the internet as we know it would cease to exist, highlighting their indispensable role in its functioning.
9. Based on Internet Network Classification
Intranet: An intranet is like a private digital space within an organization. It’s a network that connects the organization’s internal computers, servers, and resources. Think of it as a digital office where employees can collaborate, share files, and communicate.
Intranets are restricted to authorized users and are often used for sharing sensitive company information and fostering efficient teamwork.
Internet: The internet, often referred to as the “World Wide Web,” is the vast network that connects billions of devices and networks worldwide. It’s a global public network that allows individuals, businesses, and institutions to share information, access online services, and communicate across borders. The internet is what most people think of when they talk about going online.
Extranet: An extranet is like a bridge between organizations. It’s a network that connects different organizations or partners to share specific resources or collaborate on joint projects. Extranets are used for secure communication and data sharing between trusted entities while keeping other parts of their networks separate.
Dark Net: The dark net is a mysterious and hidden part of the internet. It’s not indexed by search engines and is often associated with anonymity. While it can be used for legitimate purposes, it has gained notoriety for being a hub of illegal activities. Users on the dark net typically use special software like Tor to access websites anonymously.
It’s important to note that not all activities on the dark net are illegal, but its secretive nature has led to concerns about its use.
These classifications of networks serve different purposes and illustrate the diverse landscape of interconnected digital spaces, from the public internet to private corporate intranets and even the secretive world of the dark net.
.
Conclusion: The Digital Tapestry of Computer Networks
In the intricate realm of computer networks, we’ve unraveled a digital tapestry that weaves our interconnected world together. From PANs to the global reach of WANs, from VPNs guarding our privacy to the enigmatic dark net, these networks are the lifeblood of our digital age. Understanding them isn’t just a skill; it’s the key to unlocking boundless possibilities in our interconnected world.
